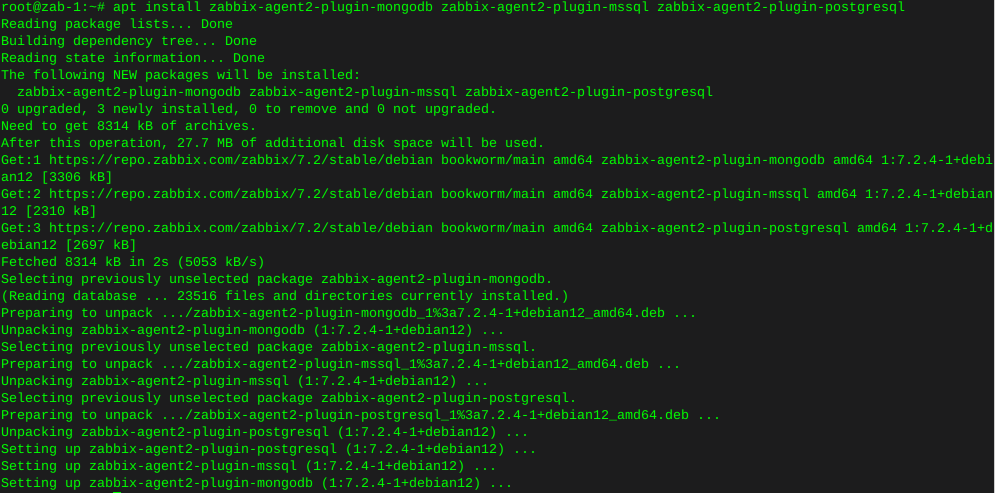
Ubiquity AP-Pro LED replacement
-
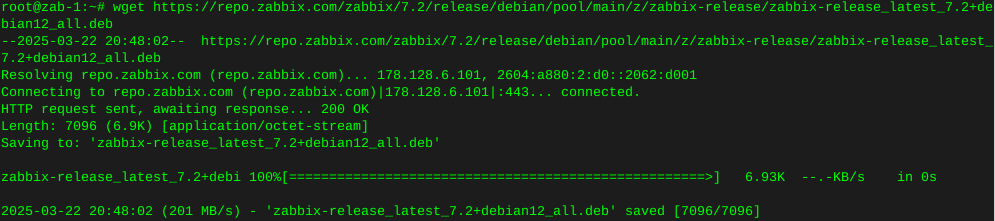
After a couple years the blue LED in the AP-Pro’s withered to a mere shadow, not that this really matters for functionality, but it does. It’s a status report.
Anyway I searched around to find the next size up from the 0603 which appear to be the original size, both the 0805 and the 0603 rates ~3v@ 20Ma. I opted to use the larger of the two. The size of the 0805 claims 2/1.25/.8 mm, where the 0603 sits 1.6/.8/.6
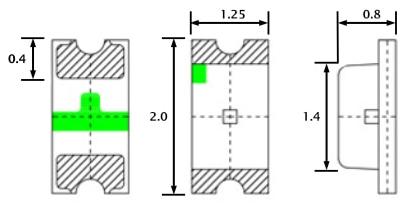
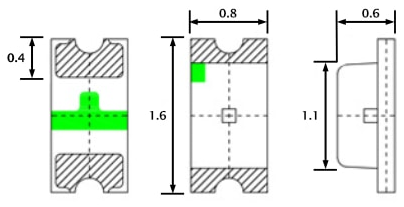
For reference here is the 0805 in my hand , and on a Lowe’s gift card. The Anode (+) is the green mark.


The job could have used a solder tip 1/4 of the smallest size I had which was ~1.5mm, as well the solder could have been 0.3mm Vs. 0.6mm

The blue LED is located at ‘D11’, the white is ‘D12’
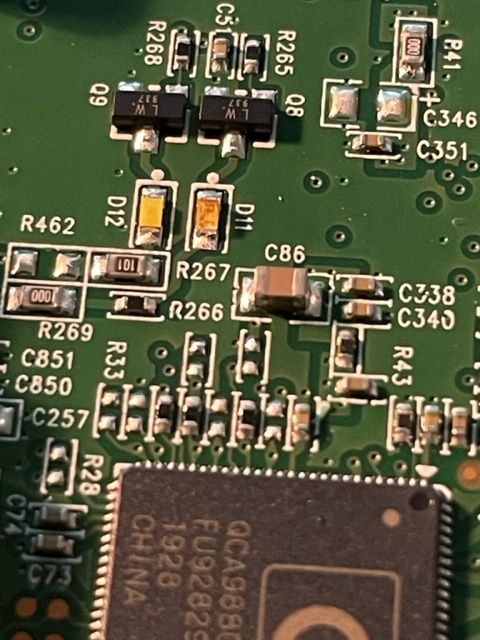
Below is the before and after replacement of the LED’s The new LED floods the lens.


At any rate, it was more difficult to spudge the cases open than the LED’s were to replace. There is a small amount of silicone type compund around the rim, and three interlocking standoffs on the case. Snapped back together as if they were happy.
Before / after


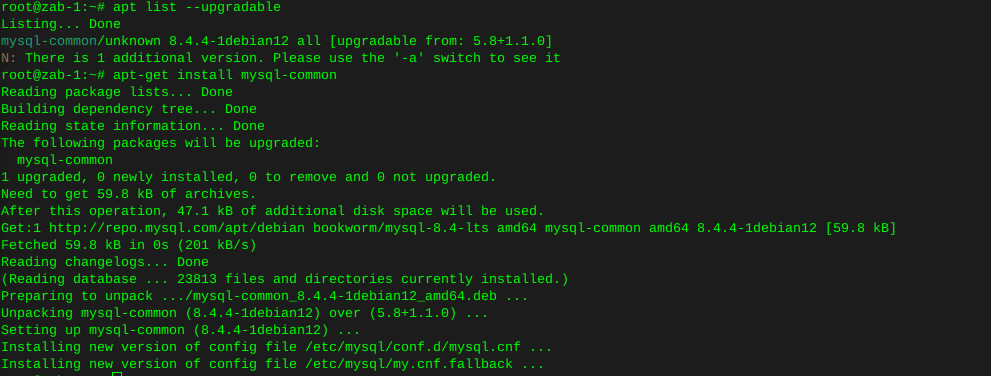
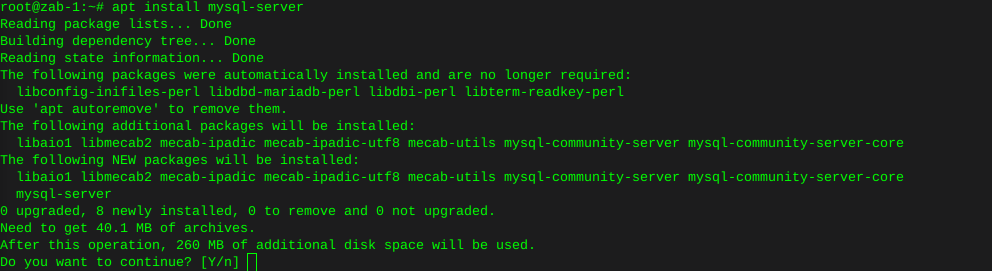
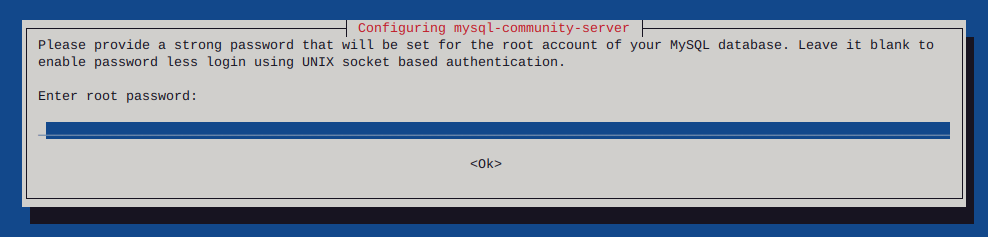
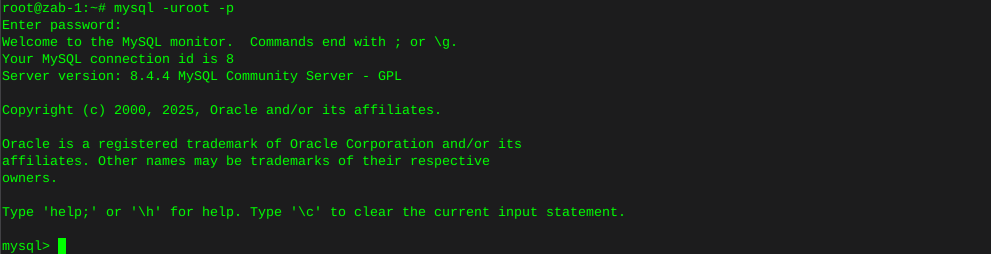
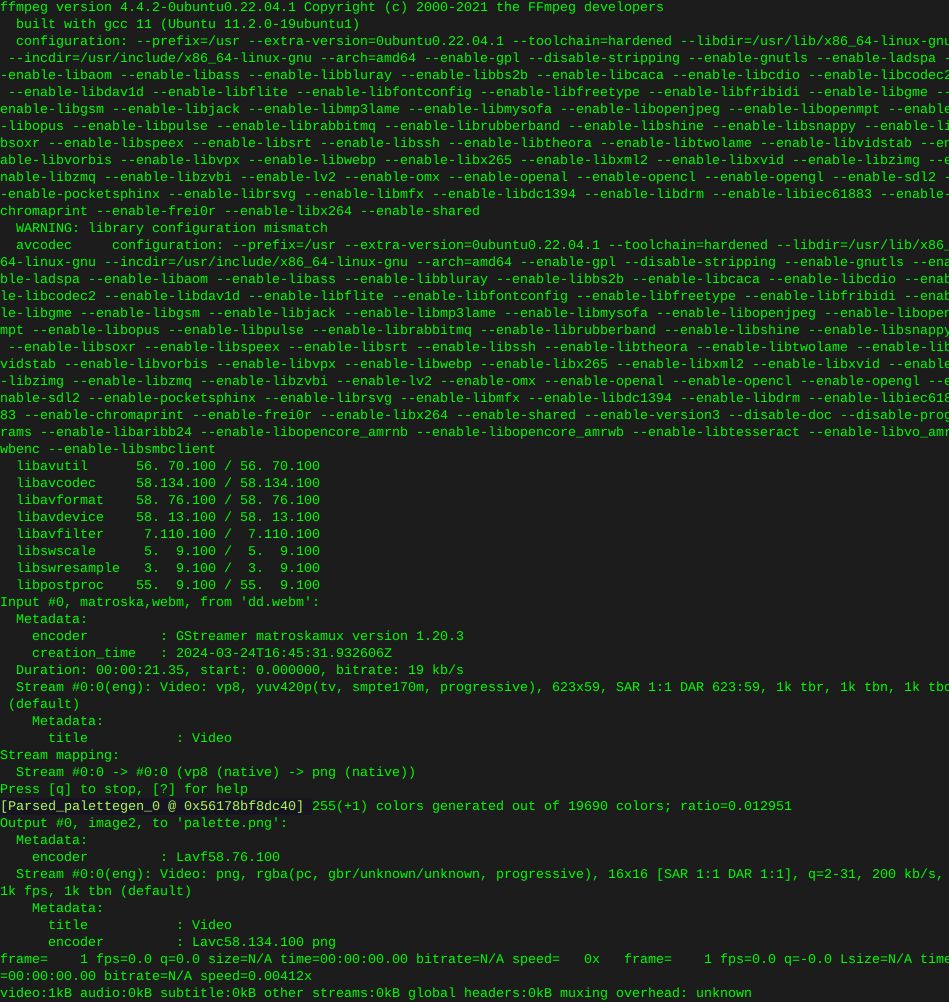
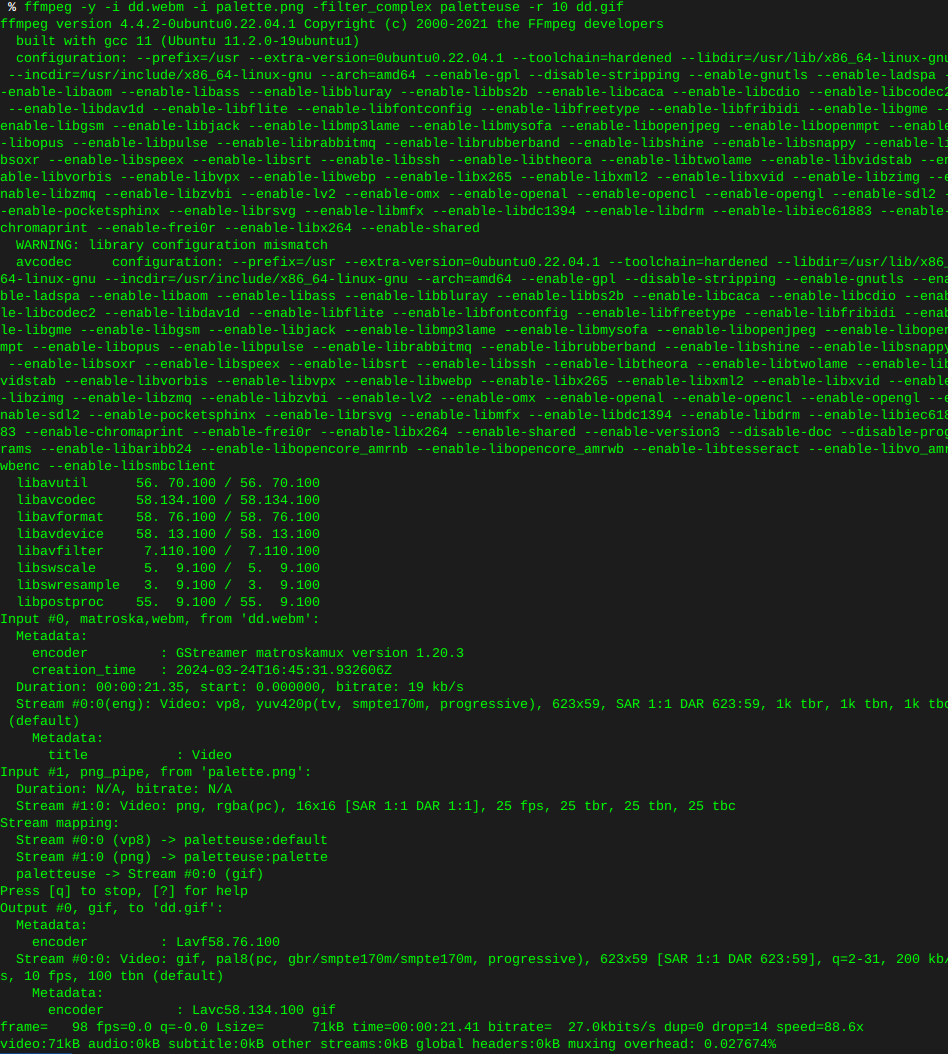
This whole thing started after running a CT of Unifi for the controller. They use a version of MariaDB that is no longer maintained, therefore the base OS cannot be updated without hacking together a system. There is a shell script someone came up with that Ubiquity is linking to, I was not entertained. Considering I’ve used the container to manage the AP’s for a while I was ready to update some hardware.
The UDM-SE wants to live in front of everything else, considering I’m a PfSense user, that was not going to happen. I gave it it’s own physical LAN port on the Netgate 4100 in it’s own VLAN, chose to set the DHCP to relay, nothing I’ve done so far allows the IP’s the DHCP server in PfSense lease to the AP clients, to pass data through the UDM. Spanning tree refused to allow me entry to the UDM when setup this way. Turning off RSTP allowed access to UDM (but only by a direct physical connection to the UDM.) likely due to the subnet difference, Loving level2.
I’ll need to segregate and run a PCAP while a client.
So for now the UDM sits on the side in it’s own VLAN corner, serving IP’s to clients in it’s own subnet. The double NAT doesn’t seem to effect throughput by any noticeable difference.

I posted this over at TestMy.net if you have any questions or comments.