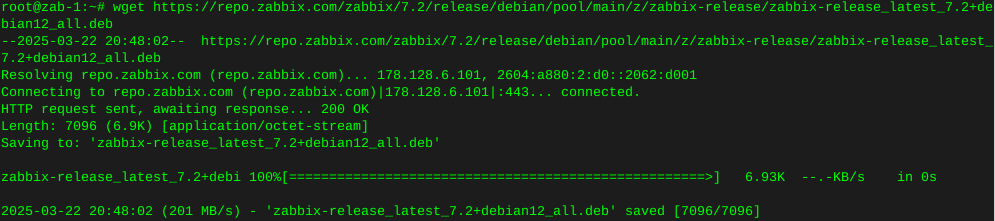
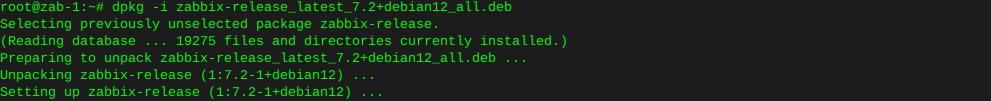
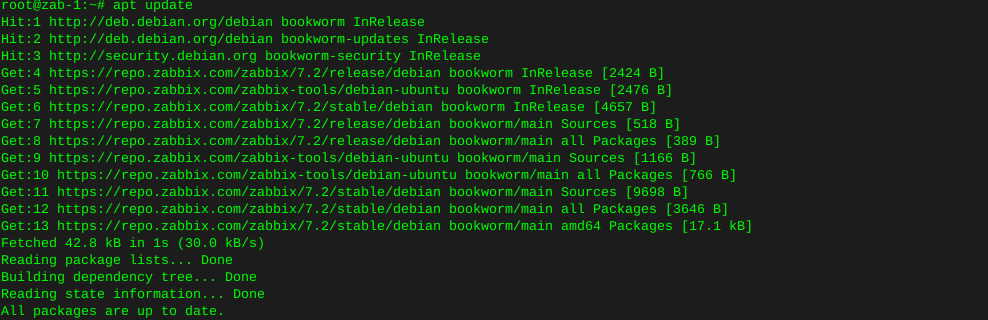
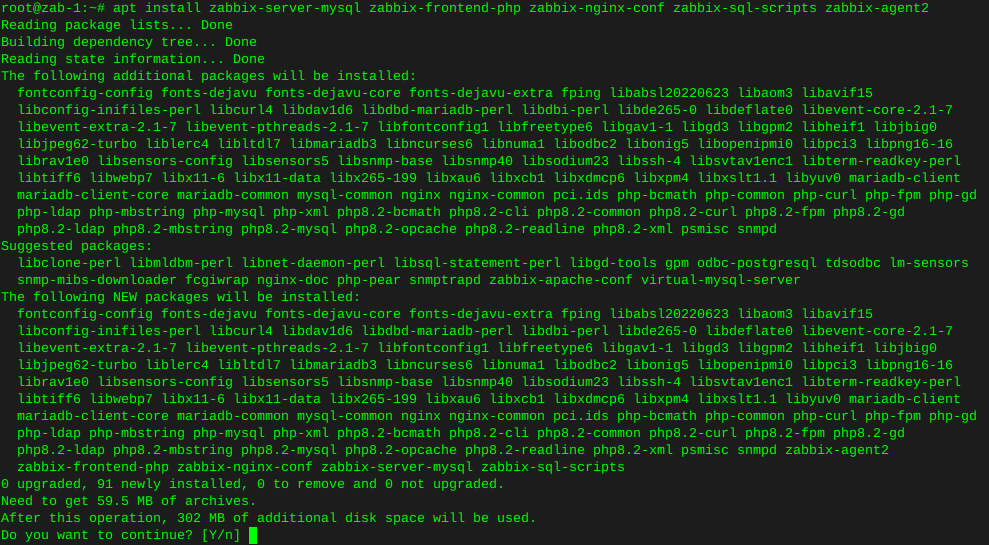
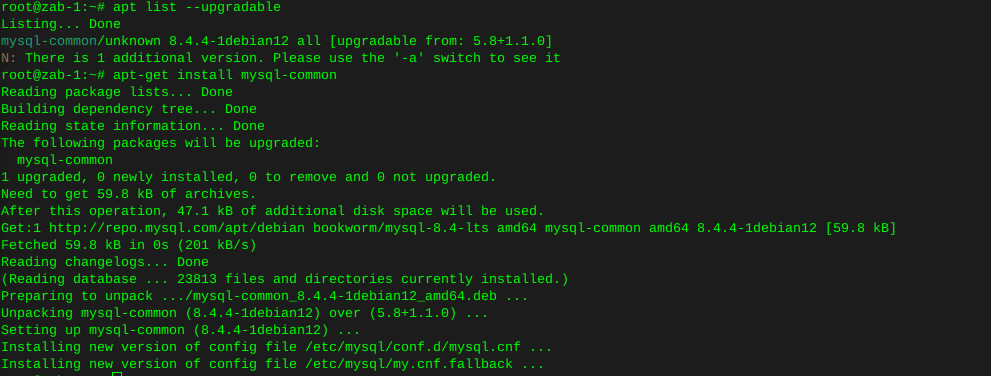
Spin up HDD in PUIS mode and wipe drive for new placement
-
Recently I came across an older DVR unit, taking into consideration I’m not one to pass up an opportunity to harvest tech, so I took the liberties I had been granted.
Just want the commands and take your chances? Skip down beyond my rambling.
Not much useful inside most of these units, but there was a mechanical HDD.
The drive is a WD5000AVVS, after a bit of googling around, I found Western Digital made these specifically for a DVR application. In other words, not really made to support a desktop environment. No reason to let that stop me from adding it for basic storage.
The drive was utilizing PUIS or Power [Up In Standby] , something WD came up with themselves, from the wiki:
Power-up in standby (PUIS) or power management 2 mode (PM2; Western Digital specific) is a SATA or Parallel ATA (aka PATA) hard disk configuration which prevents the drive from automatic spinup when power is applied. The spinup occurs later by an ATA command, only when the disk is needed, to conserve electric power[dubious – discuss] and to avoid a power consumption peak caused by a simultaneous spin-up of multiple disks.
Useful tip: Since the drive will not power up on boot, I had to connect the drive to a raid controller to get it to spin up. I’m sure there are other means, such as issuing ATA commands.
Set PUIS mode on Western Digital Hard Drive
Enter the hdparm command , for help on commands just type in:
hdparmhdparm - get/set hard disk parameters - version v9.43, by Mark Lord. Usage: hdparm [options] [device ...] Options: -a Get/set fs readahead -A Get/set the drive look-ahead flag (0/1) -b Get/set bus state (0 == off, 1 == on, 2 == tristate) -B Set Advanced Power Management setting (1-255) -c Get/set IDE 32-bit IO setting -C Check drive power mode status -d Get/set using_dma flag -D Enable/disable drive defect management -E Set cd/dvd drive speed -f Flush buffer cache for device on exit -F Flush drive write cache -g Display drive geometry -h Display terse usage information -H Read temperature from drive (Hitachi only) -i Display drive identification -I Detailed/current information directly from drive -J Get/set Western DIgital "Idle3" timeout for a WDC "Green" drive (DANGEROUS) -k Get/set keep_settings_over_reset flag (0/1) -K Set drive keep_features_over_reset flag (0/1) -L Set drive doorlock (0/1) (removable harddisks only) -m Get/set multiple sector count -M Get/set acoustic management (0-254, 128: quiet, 254: fast) -n Get/set ignore-write-errors flag (0/1) -N Get/set max visible number of sectors (HPA) (VERY DANGEROUS) -p Set PIO mode on IDE interface chipset (0,1,2,3,4,...) -P Set drive prefetch count -q Change next setting quietly -Q Get/set DMA queue_depth (if supported) -r Get/set device readonly flag (DANGEROUS to set) -R Get/set device write-read-verify flag -s Set power-up in standby flag (0/1) (DANGEROUS) -S Set standby (spindown) timeout -t Perform device read timings -T Perform cache read timings -u Get/set unmaskirq flag (0/1) -U Obsolete -v Use defaults; same as -acdgkmur for IDE drives -V Display program version and exit immediately -w Perform device reset (DANGEROUS) -W Get/set drive write-caching flag (0/1) -x Obsolete -X Set IDE xfer mode (DANGEROUS) -y Put drive in standby mode -Y Put drive to sleep -z Re-read partition table -Z Disable Seagate auto-powersaving mode --dco-freeze Freeze/lock current device configuration until next power cycle --dco-identify Read/dump device configuration identify data --dco-restore Reset device configuration back to factory defaults --direct Use O_DIRECT to bypass page cache for timings --drq-hsm-error Crash system with a "stuck DRQ" error (VERY DANGEROUS) --fallocate Create a file without writing data to disk --fibmap Show device extents (and fragmentation) for a file --fwdownload Download firmware file to drive (EXTREMELY DANGEROUS) --fwdownload-mode3 Download firmware using min-size segments (EXTREMELY DANGEROUS) --fwdownload-mode3-max Download firmware using max-size segments (EXTREMELY DANGEROUS) --fwdownload-mode7 Download firmware using a single segment (EXTREMELY DANGEROUS) --idle-immediate Idle drive immediately --idle-unload Idle immediately and unload heads --Istdin Read identify data from stdin as ASCII hex --Istdout Write identify data to stdout as ASCII hex --make-bad-sector Deliberately corrupt a sector directly on the media (VERY DANGEROUS) --offset use with -t, to begin timings at given offset (in GiB) from start of drive --prefer-ata12 Use 12-byte (instead of 16-byte) SAT commands when possible --read-sector Read and dump (in hex) a sector directly from the media --security-help Display help for ATA security commands --trim-sector-ranges Tell SSD firmware to discard unneeded data sectors: lba:count .. --trim-sector-ranges-stdin Same as above, but reads lba:count pairs from stdin --verbose Display extra diagnostics from some commands --write-sector Repair/overwrite a (possibly bad) sector directly on the media (VERY DANGEROUS)As we can see, there is a command we can utilize to change the PUIS setting of the drive:
hdparm -sOf course you must enter the device name you wish to change the settings on. So we can use:
lsblkThe lsblk command will list all block devices in the system
Which in this case spits out the following:
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT sda 8:0 0 465.8G 0 disk └─sda1 8:1 0 465.8G 0 part sdb 8:16 0 465.8G 0 disk └─sdb1 8:17 0 465.8G 0 part /media/rick/WD500GB sdc 8:32 0 465.8G 0 disk └─sdc2 8:34 0 1K 0 partThis is now that the drive is finished, formatted and partitioned in the system. Sometimes you’ll need a bit more data to make the choice as to which drive you’ll be schnookering.
So we can use lsblk flags as well.
lsblk --output MODE,NAME,FSTYPE,LABEL,UUIDWhich spits out the following infos:
MODE NAME FSTYPE LABEL UUID brw-rw---- sda isw_raid_member brw-rw---- └─sda1 brw-rw---- sdb brw-rw---- └─sdb1 ext4 WD500GB 4e423629-51e8-41b3-a9be-9c9af4d31732 brw-rw---- sdc isw_raid_member brw-rw---- └─sdc2Well I know the two disks which say raid member are not it, and at this point there is only three block devices in the system, so I’ll use /dev/sdb
If we look at the hdparm command to turn on or off PUIS, it states the two options which are 0/1 = Off or On
So the command I’ll run on /dev/sdb to wake it up with hdparm is:
hdparm -s 0 /dev/sdbDone with that jazz. The drive should spin up when powered on. Lest, we are not finished here. We should clean things up a bit.
For simplicity I enjoy the shred command, plus it sounds serious, which it is.
To find shred commands, we just run:
shred --helpWhich pukes out this:
Usage: shred [OPTION]... FILE... Overwrite the specified FILE(s) repeatedly, in order to make it harder for even very expensive hardware probing to recover the data. Mandatory arguments to long options are mandatory for short options too. -f, --force change permissions to allow writing if necessary -n, --iterations=N overwrite N times instead of the default (3) --random-source=FILE get random bytes from FILE -s, --size=N shred this many bytes (suffixes like K, M, G accepted) -u, --remove[=HOW] truncate and remove file after overwriting; See below -v, --verbose show progress -x, --exact do not round file sizes up to the next full block; this is the default for non-regular files -z, --zero add a final overwrite with zeros to hide shredding --help display this help and exit --version output version information and exitRemember, this can be done on any drive, so everything and anything will be lost to the abyss forever. Pay attention to which drive letter / name you are using.
The default pass is 25 times, yea, I’ve never needed a 25 pass random write scrub and I hope never to. So we can use the flag -n to limit how many passes shred does.
I enjoy seeing output, so I’ll use the -v or, Verbose / noisy output flag as well.
I also had no idea what permissions were set, so I used the -f or Force flag As stated, this changes permissions to allow for the write procedure if required.
If your obsessive about keeping things straight, use the -z flag also, this will add one more pass after ‘shredding’ and write zero’s across the drive. Instead of having the drive look as if someone intentionally randomly repeatedly wrote ‘junk’ to it. Just make your bed.
The command I used to wipe the drive was as follows:
shred -n 5 -v -f -z /dev/sdbLet the shredding begin, here is the initial output:
shred: /dev/sdb: pass 1/6 (random)... shred: /dev/sdb: pass 1/6 (random)...330MiB/466GiB 0% shred: /dev/sdb: pass 1/6 (random)...687MiB/466GiB 0% shred: /dev/sdb: pass 1/6 (random)...1.0GiB/466GiB 0% shred: /dev/sdb: pass 1/6 (random)...1.3GiB/466GiB 0% shred: /dev/sdb: pass 1/6 (random)...1.7GiB/466GiB 0% shred: /dev/sdb: pass 1/6 (random)...2.1GiB/466GiB 0% shred: /dev/sdb: pass 1/6 (random)...2.4GiB/466GiB 0% shred: /dev/sdb: pass 1/6 (random)...2.8GiB/466GiB 0% shred: /dev/sdb: pass 1/6 (random)...3.1GiB/466GiB 0%And this goes on for quite some time. Notice we used the -n 5 flag, for five passes, yet we can see shred is currently on pass 1/6. Good, this means the last pass will be all zeros.
Go do something else until your ready to format and partition the drive. Let it run!
-
For a more comprehensive or detailed guide, as to securely wiping a drive, visit nixCraft-how-do-i-permanently-erase-hard-disk